When referring to computer networking, the term "networking" describes the act of connecting various devices, such as computers, servers, and printers, to one another to share resources and exchange data. Through networking, devices may talk with one another and share resources like files and printers as well as internet access.
History
The history of computer networking dates back to the 1960s, with the development of early packet-switching technologies. The first wide-area network (WAN) was the ARPANET, which was created by the Advanced Research Projects Agency Network (ARPANET) of the United States Department of Defense. It was first operational in 1969 and was used primarily for research and education purposes.
The first ARPANET link was established in October 1969, between the University of California, Los Angeles (UCLA) and the Stanford Research Institute (SRI). Over the next few years, several other universities and research institutions were connected to the network, including the University of California, Santa Barbara, the University of Utah, and the Massachusetts Institute of Technology (MIT).
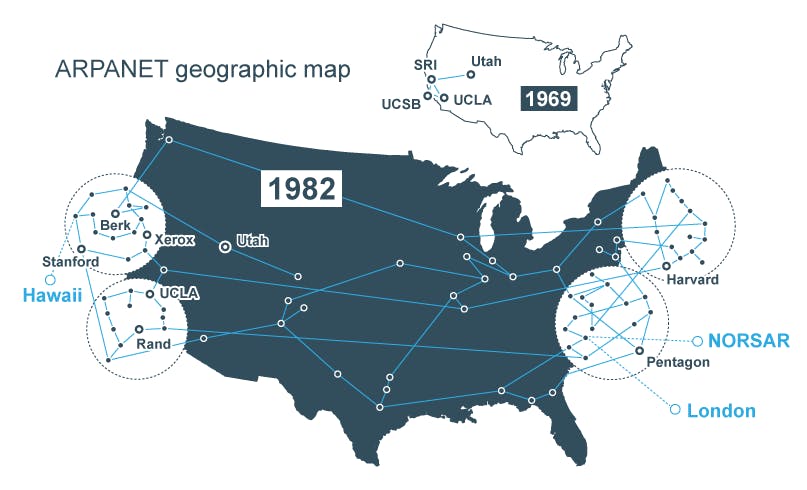
ARPANET used the Network Control Program (NCP) as its initial host-to-host protocol, later replaced by the Transmission Control Protocol/Internet Protocol (TCP/IP) in 1982. This change marked the transition from the ARPANET to the Internet as we know it today.
INTERNET
We are talking a lot about the internet. Now the question arises: what is the internet, how does it work, who owns it, and does anyone really own the internet—does any particular person, organization, or government own or run the internet?
The answer is simple: The Internet is a global network of interconnected computer systems that use the Internet Protocol (IP) to transmit and receive data. It is a network of networks that consists of millions of private, public, academic, business, and government networks of local to global scope that is linked by a broad array of electronic, wireless, and optical networking technologies.
It is important to note that the Internet is not owned by any single entity or organization. It is a decentralized system, which means that no one person, organization, or government controls it.
Internet Society
However, there must be something controlling the internet. Internet Society is something from which we can contribute openly -
The Internet Society (ISOC) is a non-profit organization that promotes the open development, evolution, and use of the Internet for the benefit of all people throughout the world. It was founded in 1992 and is based in Reston, Virginia, United States. The Internet Society's mission is to promote the open development, evolution, and use of the Internet for the benefit of all people throughout the world. It aims to do this by providing leadership in addressing issues that confront the future of the Internet, and by engaging with a global community of stakeholders to develop policies and programs that promote the Internet's growth and evolution. The Internet Society has members and supporters from around the world and works closely with other organizations to promote the open development of the Internet.
Computer Network
A computer network is a collection of interconnected devices, such as computers, servers, switches, routers, and other devices, that are connected together to share resources and exchange information. These networks can be wired or wireless and vary in size from small local area networks (LANs) that connect a few devices in a single location to large wide area networks (WANs) that connect devices across multiple locations. The main goal of computer networks is to enable the sharing of resources and information between devices, which can lead to increased productivity, collaboration, and communication.
There are several types of computer networks, each with its characteristics and uses. Some of the most common types include:
Local Area Network (LAN): A LAN is a network that connects computers and devices in a small geographic area, such as a home, office, or building. LANs are typically used to share resources such as printers and files, and to facilitate communication between users.
Wide Area Network (WAN): A WAN is a network that connects computers and devices over a larger geographic area, such as a city, country, or the entire world. WANs are typically used to connect LANs, and to provide remote access to resources and services.
Metropolitan Area Network (MAN): A MAN is a network that connects computers and devices in a metropolitan area, such as a city or town. MANs are typically used to connect LANs and WANs, and to provide high-speed connectivity for businesses and organizations.
Wireless Network: A wireless network uses radio waves to connect devices without the need for physical cables. Wireless networks include Wi-Fi networks, which are commonly used in homes, offices, and public places, and cellular networks, which are used to connect mobile devices to the Internet.
Personal Area Network (PAN): A PAN is a small network that connects devices that are close to a person, such as a personal computer, smartphone, and smartwatch.
Cloud Network: A Cloud Network is a network that uses cloud computing resources to provide services over the Internet. Cloud networks allow users to access resources such as storage, applications, and computing power on-demand, without having to maintain their infrastructure.
Virtual Private Network (VPN): A VPN is a network that allows users to securely connect to a private network over the Internet. VPNs are often used by businesses and organizations to provide remote access to their internal networks and to protect sensitive data from unauthorized access.
Each type of network has its own set of protocols and technologies that govern how devices communicate and share resources, such as TCP/IP, Ethernet, and Wifi.
Computer Network Model
Computer network models provide a way to understand and predict the behavior of a network, allowing network administrators to make informed decisions about how to design, operate, and maintain the network.
There are several types of network models, each with its characteristics and uses.
Protocol Models: Protocol models are used to simulate and analyze the behavior of network protocols, such as TCP/IP and OSI. These models can be used to analyze the performance of different protocols, and to identify potential issues or bottlenecks.
Queueing Models: Queueing models are used to analyze the behavior of network queues, such as those found in routers and switches. These models can be used to predict the performance of a network under different conditions, such as high traffic loads.
Topology Models: Topology models are used to represent the physical and logical structure of a network. These models can be used to analyze the behavior of different network topologies, such as bus, ring, and star.
Traffic Models: Traffic models are used to represent the flow of data in a network. These models can be used to predict the behavior of a network under different traffic patterns, such as a burst or steady traffic.
Analytical Models: Analytical models use mathematical equations to describe the behavior of a network. These models can be used to make predictions about network performance, such as throughput and delay, and to analyze the impact of different network parameters, such as packet size and transmission rate.
Simulation Models: Simulation models use computer programs to mimic the behavior of a network. These models can be used to test different network configurations, protocols, and traffic patterns, and to identify potential issues or bottlenecks.
OSI Model
The OSI (Open Systems Interconnection) model is a framework that is used to understand how data is transmitted over a network. It is a seven-layer model that explains how various technologies and protocols interact to make it possible for data to be exchanged between devices on a network. The OSI model is frequently employed as a reference model because it provides a broad overview of networking that is unrelated to any one particular technology.
There are seven OSI layers and it is divided into two layers: upper layers and lower layers.
The upper layers deal primarily with the application-level functionality of the network. They are responsible for enabling communication between applications and providing services such as data encryption, compression, and session management. The upper layers of the OSI model are:
Application Layer: The Application Layer is the topmost layer of the OSI model and provides interfaces and services that allow users and programs to access the network's resources. It is the point of interaction between the user and the network and is responsible for handling the functions that are specific to the application, such as file transfers, email, and remote login, and it provides services such as directory services, network management, and distributed object management, it also manages the flow of data between the application and the network, ensuring that the data is sent and received in the correct format and that any errors are handled appropriately.
Presentation Layer: The Presentation Layer is responsible for converting data into a format that can be understood by the Application layer, it may include character code conversion, data compression, and encryption, and it provides a common format for the data being exchanged between devices, allowing them to communicate effectively even if they are using different data formats or compression techniques.
Session Layer: The Session Layer is responsible for managing the communication between devices, establishing and maintaining a logical connection between them, and ensuring that data is sent and received in the correct order. It creates a unique identifier, called a session ID, to identify the session and all the communications that take place within it. The layer also provides synchronization, ensures data is received in the same order it was sent and deals with any issues that may arise during the session. Additionally, it provides security for the session by providing authentication and access control for the devices participating in the session and encrypting the communication between them.
The lower layers deal primarily with the transport-level functionality of the network. They are responsible for providing services such as error checking, flow control, and addressing. They are also responsible for moving data across the network.
Transport Layer: The Transport Layer is responsible for providing end-to-end communication services between devices on a network. It ensures that data is delivered reliably and in the correct order between the source and destination devices. It also provides flow control, segmentation and reassembly of data, multiplexing and demultiplexing, and Quality of Service (QoS). It breaks up large data streams into smaller segments, called packets, for easier transmission and reassembles them back into their original form at the destination. It also allows multiple applications to share a single network connection by assigning each application a unique port number and separating incoming data streams into their corresponding applications at the destination.
Network Layer: The Network Layer is responsible for providing logical addressing and routing of data packets between devices on a network. It determines the best path for data to travel from the source device to the destination device, and for breaking up the data into smaller packets, called datagrams, for easier transmission. It also provides logical addressing, fragmentation and reassembly of packets and Quality of Service (QoS). It uses routing algorithms to determine the best path for data to travel and to manage the flow of data through the network.
Data Link Layer: The Data Link Layer is responsible for providing reliable data transfer over the physical link established by the Physical Layer. It provides the means for the logical organization of data into packets, called frames, and the control of the flow of these frames between devices. It also handles error detection and correction, flow control, addressing of devices and management of the media access control (MAC) protocol. It also ensures that the frames are sent and received in the correct order and that any errors in the frames are handled appropriately.
Physical Layer: The Physical Layer is the lowest layer of the OSI model and it is responsible for transmitting raw bits over the physical medium, it defines the mechanical, electrical, and functional characteristics of the physical connections between devices, such as cables and connectors, as well as the timing and signaling requirements for communication. It also handles the physical connections between devices, including the installation, configuration, and maintenance of the physical connection, as well as the testing and troubleshooting of any issues that may arise. It deals with the modulation and demodulation of the signal, converting the data into a signal that can be transmitted over the physical medium and back to the original data.

